It is a vexed topic: IT security. The thought of attacks on one's own operating system and sensitive data is extremely unpleasant. Some people prefer not to deal with the undesirable scenarios at all and simply hope for the best. Not a good idea, because the current figures show that protecting one's own data and systems is immensely important. Thanks to IT Managed Services, this is not an insurmountable task, but a To Do that can easily be done – promised!
Logistics companies are particularly often in the spotlight when it comes to threats from hacker attacks, because if an attack succeeds, the effects are often felt in numerous locations around the world and billions of euros in damage are incurred. In the second half of 2021 alone, 27 attacks on companies in the transport and logistics sector were successful, three of which happened in Germany. These were not companies that had wandered naively through the digital world and had not even bothered with their IT security, no: despite protective measures taken, a fraction of the attempted attacks was successful and put the affected companies in a severe predicament, as the methods of attack are becoming increasingly perfidious. However, this introduction is not intended to paint a pessimistic picture, but to underline the importance of firewall managed services and show how they make a major contribution to improved protection and always up to date security systems – the explanation follows immediately.
"Dear Mr Mayer. One of your passwords has been decrypted. In order for your data security to be restored, you must act immediately. Click here to view the list of published data". A phishing email could look like this or something similar. Long gone are the days of spelling and grammatical errors, strange umlauts or dubious senders that made it easy to identify a fake mail. Nowadays, virtual attacks are becoming more and more sophisticated and are not always easy to detect. Users are therefore still the easiest entry point into the system: Just one wrong click or connecting to what only appears to be a genuine WLAN hotspot, and one flimsy attachment later, the door is opened for hackers to enter the system. Regular training and sensitization of employees is therefore a top priority so that the risk of attack can be kept as low as possible. A look at the "10 tips to increase IT security" is helpful in this regard.
The Internet is no longer new territory for any of us – but the entire IT security sector has grown steadily along with it. The task of updating the company's own firewall or exploring new possibilities for data protection can quickly become overwhelming – after all, there is hardly a limit to what can be done. So where to start?
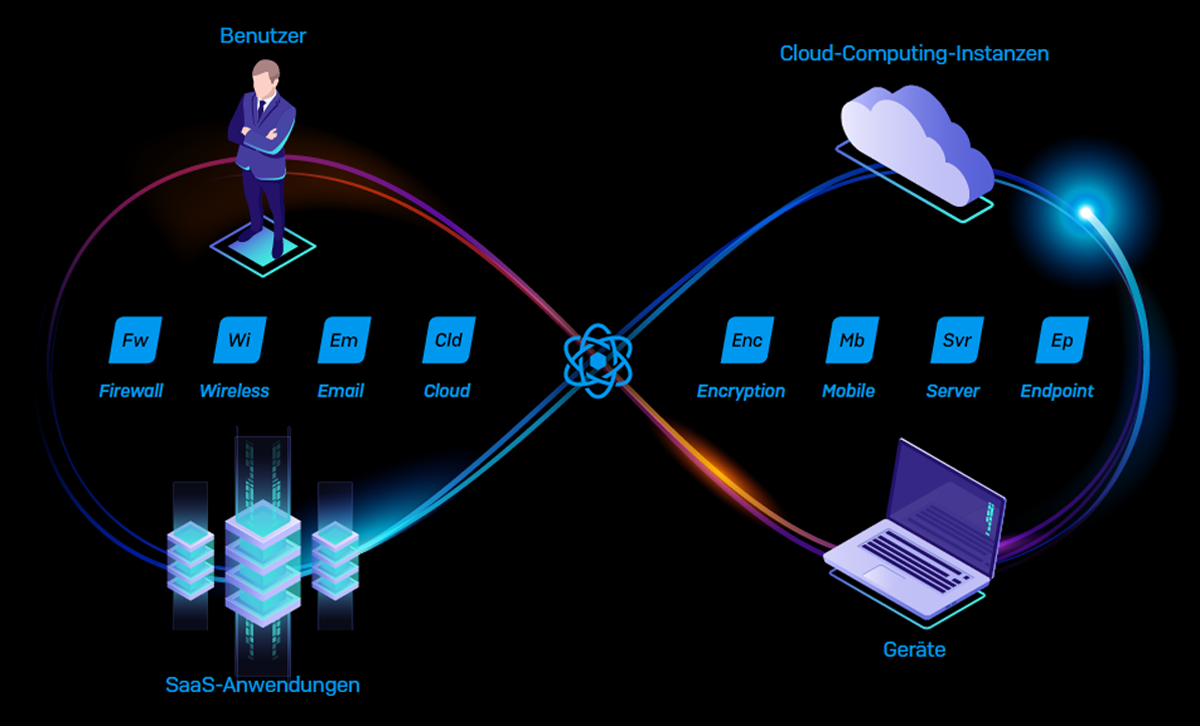
It is certainly not necessary to cover the entire alphabet of IT security, it is sufficient to start with the most important factors – once the basis has been laid, there is always the option of constantly building up protection. The absolute minimum here is a sensible firewall including anti-virus protection. Separation of the individual systems, so that in the event of an attack not all systems are directly affected, sandboxing modules, spam filtering or controlled antivirus solutions then represent subsequent steps on the ladder of IT security in logistics. In any case, it is worthwhile to commission experts with the company's own cyber security.
Once the start has been made, the next steps are to be taken: With the choice of a managed service provider, the roughest work is already done – because from now on, professionals will take care of your data security so that you and your employees can fully concentrate on your core tasks. During a workshop, an evaluation matrix is used to analyze the current situation so that the appropriate options can be found for the respective requirements. It is up to you to decide whether you want to keep the reins in your own hands as much as possible or whether you prefer to leave the firewall, including the add-on modules, completely in the hands of an external company. Should the company and IT security drift too far apart, modules can be added, or the model changed at any time.
A managed service provider works with a monitoring platform to secure your business.
Do I want to outsource all my data and systems to a cloud? Does the path rather lead to a data centre where the data is stored or is an on-site solution in a local environment preferred? In order to find the right solution for each company, here is a brief summary of the three most common categories, between which hybrid solutions can of course also be found:
- Cloud
One of THE terms of the digital age is the cloud – almost everyone knows and uses it in some form. Especially in a professional context, this data solution has a lot to offer: It is the "all-round carefree package", so to speak. The cloud is like a toolbox that can be used. The individual modules can be used as needed; however, they cannot be customised – similar to a purchased tool. This reduces the cost factor for customers. The other side of the coin, however, is surely that certain options are already defined by the cloud providers, so that the freedom of design is limited, for example, when setting up a spam filter for your mail programmes. However, for those who want absolute data security with the lowest possible excess, this option is ideal.
- Data centre
The freedom of design is higher with this option than with the cloud. If you use the services of a data centre where your data servers are located, then as a company you benefit from the firewall and other protective mechanisms that directly block access to all data as the virtual entrance door of the data centre. Nevertheless, you always have full decision-making power, for example with regard to the type and mode of operation of a spam filter or other protection modules.
- On-site
solution The minimum-security standard is automatically higher with the two previous solutions than with the flexible on-site solution, as the motto here is "everything’s optional, nothing’s a must". Of course, there are urgent recommendations regarding the components required for basic protection, but a slow approach to different levels of protection is also possible. Especially for smaller companies, for which a cloud solution would be too costly, this option is worthwhile, where the data remains with you in the company and is secured there in the best possible way.
Effective security solutions offer comprehensive next-gen protection.
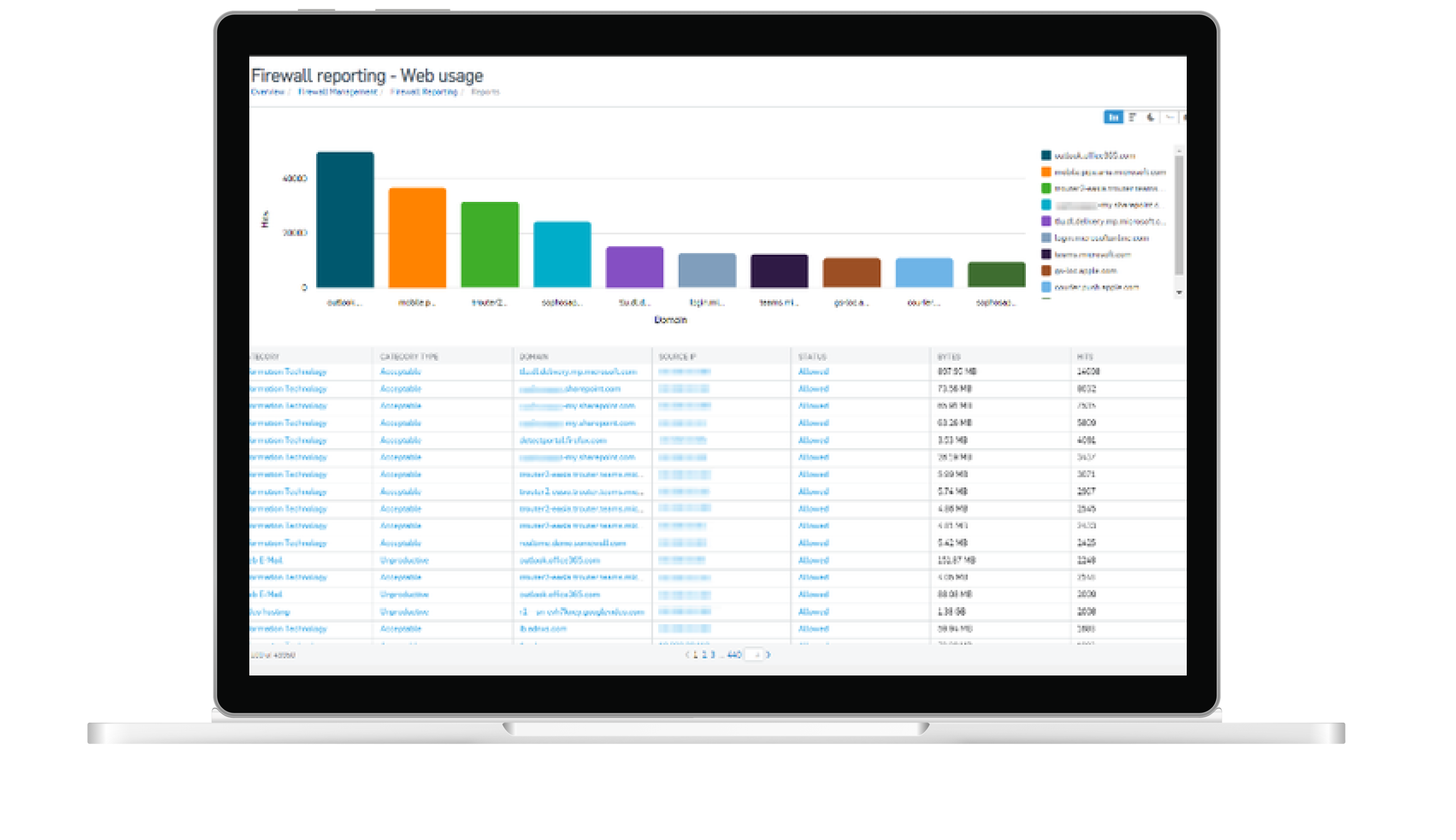
The general level of protection of the digital infrastructure is significantly increased using the latest firewall technology. The next-generation firewall, which is used by the managed service provider both in the cloud solution and in the data centre or local environment, meets the highest security standards and is considered "state of the art", i.e., currently the best of the best. It heralds the third generation of firewall technology, detecting and blocking even the most sophisticated attacks by enforcing security policies at the application, port and protocol levels. Thanks to detailed data analysis, malicious software is detected even if the traffic initially appears harmless. Protective mechanisms such as sandboxing, HTTPs inspection, intrusion detection system (IDS) or intrusion prevention system (IPS) and deep packet inspection (DPI) make this possible.
Between 4,000 and 5,000 cyber-attacks on customers' systems are recorded by a data centre on average every day. It is easy to imagine what would happen without the additional protection in front of the digital main entrance. In the rare event that an attack succeeds despite high security standards and, for example, an encryption Trojan gains access to the company's data, there are emergency scenarios that take effect immediately thanks to the IT managed service provider.
First, the IT forensics department searches for clues: Where does the attack come from? Which systems are affected? What method of attack was used? The horror scenario par excellence, in which the hackers use ransomware to encrypt data on the company's own servers and subsequently extort a ransom, should be avoided at all costs; sometimes the solution can be disconnection from the network. This is because encryption Trojans now often also look for backup systems because it is known that they can cause much greater damage there. Separating the systems is accordingly important: The affected area of the system is isolated so that the ransomware cannot access other areas of the digital corporate structure – this protects the operational systems, for example. The fastest possible restoration of a backup is initiated, which, depending on the company's requirements, can be a so-called instant recovery (the backup can be made operational within a minute) or a somewhat more protracted process.
In the cloud as well as in the data centre, plans and procedures for these emergency scenarios are defined by the IT service providers, who decide which solution is best when "building" the module. If one has opted for the more flexible on-site solution, then there is more freedom of choice here again, so that the emergency scenario can be developed and freely designed by oneself. Priorities can thus be set easily.
If things get dicey and a fire breaks out, it is not only a danger for the real estate, but especially for the hardware, including sensitive data. For this reason, too, it makes sense to save backups in different locations and to regularly check their functionality so as not to experience any nasty surprises.